Now even YouTube serves ads with CPU-draining cryptocurrency miners
Ad campaign lets attackers profit while unwitting users watch videos.
DAN GOODIN - 1/26/2018, 1:27 PM
YouTube was recently caught displaying ads that covertly leach off visitors' CPUs and electricity to generate digital currency on behalf of anonymous attackers, it was widely reported.
Word of the abusive ads started no later than Tuesday, as people took to social media sites to complain their antivirus programs were detecting cryptocurrency mining code when they visited YouTube. The warnings came even when people changed the browser they were using, and the warnings seemed to be limited to times when users were on YouTube.
On Friday, researchers with antivirus provider Trend Micro said the ads helped drive a more than three-fold spike in Web miner detections. They said the attackers behind the ads were abusing Google's DoubleClick ad platform to display them to YouTube visitors in select countries, including Japan, France, Taiwan, Italy, and Spain.
The ads contain JavaScript that mines the digital coin known as Monero. In nine out of 10 cases, the ads will use publicly available JavaScript provided by Coinhive, a cryptocurrency-mining service that's controversial because it allows subscribers to profit by surreptitiously using other people's computers. The remaining 10 percent of the time, the YouTube ads use private mining JavaScript that saves the attackers the 30 percent cut Coinhive takes. Both scripts are programmed to consume 80 percent of a visitor's CPU, leaving just barely enough resources for it to function.
"YouTube was likely targeted because users are typically on the site for an extended period of time," independent security researcher Troy Mursch told Ars. "This is a prime target for cryptojacking malware, because the longer the users are mining for cryptocurrency the more money is made." Mursch said a campaign from September that used the Showtime website to deliver cryptocurrency-mining ads is another example of attackers targeting a video site.
To add insult to injury, the malicious JavaScript in at least some cases was accompanied by graphics that displayed ads for fake AV programs, which scam people out of money and often install malware when they are run.
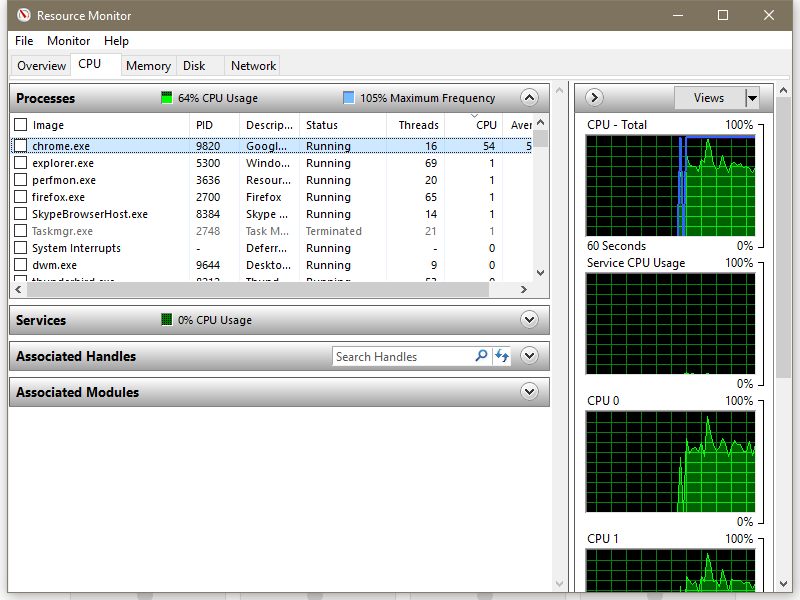
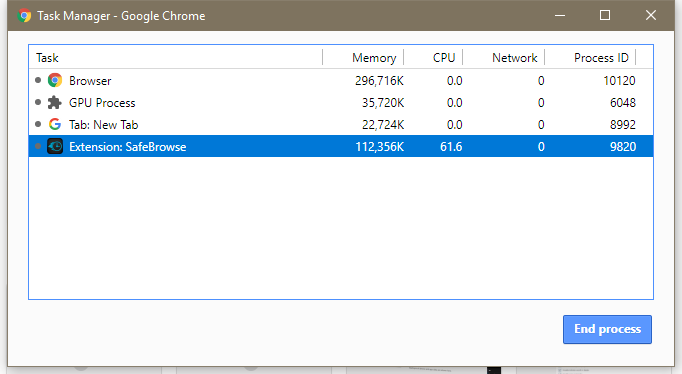
The above ad was posted on Tuesday. Like the ads analyzed by Trend Micro and posted on social media, it mined Monero coins on behalf of someone with the Coinhive site key of "h7axC8ytzLJhIxxvIHMeC0Iw0SPoDwCK." It's not possible to know how many coins the user has generated so far. Trend Micro said the campaign started January 18. In an e-mail sent as this post was going live, a Google representative wrote:
Mining cryptocurrency through ads is a relatively new form of abuse that violates our policies and one that we’ve been monitoring actively. We enforce our policies through a multi-layered detection system across our platforms which we update as new threats emerge. In this case, the ads were blocked in less than two hours and the malicious actors were quickly removed from our platforms.
It wasn't clear what the representative meant when saying the ads were blocked in less than two hours. Evidence supplied by Trend Micro and on social media showed various ads containing substantially the same JavaScript ran for as long as a week. The representative didn't respond to follow-up questions seeking a timeline of when the abusive ads started and ended.
As the problem of Web-based cryptomining has surged to almost epidemic proportions, a variety of AV programs have started warning of cryptocurrency-mining scripts hosted on websites and giving users the option of blocking the activity. While drive-by cryptocurrency mining is an abuse that drains visitors' electricity and computing resources, there's no indication that it installs ransomware or other types of malware, as long as people don't click on malicious downloads.
This post was updated to add comment from Google.
https://arstechnica.com/information...-ads-with-cpu-draining-cryptocurrency-miners/
Cryptojacking craze that drains your CPU now done by 2,500 sites
Android apps with millions of Google Play downloads also crash the party
A researcher has documented almost 2,500 sites that are actively running cryptocurrency mining code in the browsers of unsuspecting visitors, a finding that suggests the unethical and possibly illegal practice has only picked up steam since it came to light a few weeks ago.
Willem de Groot, an independent security researcher who reported the findings Tuesday, told Ars that he believes all of the 2,496 sites he tracked are running out-of-date software with known security vulnerabilities that have been exploited to give attackers control. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. About 80 percent of those sites, he added, also contain other types of malware that can steal visitors' payment card details.
"Apparently, cyberthieves are squeezing every penny out of their confiscated assets," he said.
One of the affected sites is shop.subaru.com.au. When I visited the site on Tuesday, the fan on my MacBook Pro, which I hadn't heard in months, soon started whirring. The activity monitor showed that about 95 percent of the CPU load was being consumed. As soon as I closed the site, the load dropped to about 9 percent. Besides putting a noticeable strain on my computer, the site also draws additional electricity from my office. The arrangement allows the attackers to reap the benefit of my hardware and electricity without providing anything to me in return. A recent report from security firm Trustwave's SpiderLabs estimated that the electricity cost for a single computer could range from about $2.90 to $5 per month, presumably if the cryptomining page was left open and running continuously over that time. The figure doesn't include the wear and tear on hardware as it performs complex mathematical problems required to generate the digital coins.
A surge of sites and apps are exhausting your CPU to mine cryptocurrencyThe site that makes all of this possible is Coinhive.com, which Ars covered last week. It offers an easy-to-use programming interface that any website can use to turn visitors' computers into vehicles for generating—or in the parlance of cryptocurrency people, mining—Monero. Coinhive gives participating sites a tiny cut of the proceeds and pockets the rest. Coinhive doesn't require that sites provide any notice to users.
de Groot said that about 85 percent of the 2,496 sites he tracked are generating currency on behalf of just two Coinhive accounts. Depending on the total number of visitors, the amount of time they stay on an affected site, and the power of their computers, the revenue collected by those accounts could be considerable, as would be the total amount of additional charges those accounts made to visitors' electric bills. The remaining 15 percent were spread over additional Coinhive accounts, but de Groot has evidence suggesting those accounts are controlled by a single individual or group. Most of the affected sites concealed the connection to Coinhive by adding a link to the domain siteverification.online or one masquerading as a Sucuri firewall. Those disguised sites, in turn, hosted the crypto-mining JavaScript that interacted with Coinhive.
de Groot's findings suggest that drive-by cryptomining has grown more widespread in the week since Ars first covered it or at least that the phenomenon shows no signs of abating. The earlier Ars article cited research from security firm Sucuri that found 500 sites running hacked versions of the WordPress content management system that were participating in the Coinhive mining. Ars also reported that two Android apps with as many as 50,000 downloads from Google Play had recently been caught putting cryptominers inside hidden browser windows. On Wednesday, researchers from Ixia reported finding two additional such apps with as many as 15 million downloads combined. (In fairness, one of the apps informed users it would use their phone's idle time to generate coins and provided a way for that default setting to be turned off. The apps have since been modified to curtail the practice.)
There are other indications that the in-browser cryptomining racket is getting worse. In a report published Tuesday, endpoint security provider Malwarebytes said that on average it performs about 8 million blocks per day to unauthorized mining pages.
People who want to avoid these cryptojacking scams can use Malwarebytes or another antivirus program that blocks abusive pages, install this Chrome extension, or update their computer host file to block coinhive.com and other sites known to facilitate unauthorized mining. As the phenomenon continues to grow and attract copycat services, blocklists will likely have to be updated, requiring regular updates to blocklists as well
https://arstechnica.com/information...s-cpus-picks-up-steam-with-aid-of-2500-sites/
Ad campaign lets attackers profit while unwitting users watch videos.
DAN GOODIN - 1/26/2018, 1:27 PM
YouTube was recently caught displaying ads that covertly leach off visitors' CPUs and electricity to generate digital currency on behalf of anonymous attackers, it was widely reported.
Word of the abusive ads started no later than Tuesday, as people took to social media sites to complain their antivirus programs were detecting cryptocurrency mining code when they visited YouTube. The warnings came even when people changed the browser they were using, and the warnings seemed to be limited to times when users were on YouTube.
On Friday, researchers with antivirus provider Trend Micro said the ads helped drive a more than three-fold spike in Web miner detections. They said the attackers behind the ads were abusing Google's DoubleClick ad platform to display them to YouTube visitors in select countries, including Japan, France, Taiwan, Italy, and Spain.
The ads contain JavaScript that mines the digital coin known as Monero. In nine out of 10 cases, the ads will use publicly available JavaScript provided by Coinhive, a cryptocurrency-mining service that's controversial because it allows subscribers to profit by surreptitiously using other people's computers. The remaining 10 percent of the time, the YouTube ads use private mining JavaScript that saves the attackers the 30 percent cut Coinhive takes. Both scripts are programmed to consume 80 percent of a visitor's CPU, leaving just barely enough resources for it to function.
"YouTube was likely targeted because users are typically on the site for an extended period of time," independent security researcher Troy Mursch told Ars. "This is a prime target for cryptojacking malware, because the longer the users are mining for cryptocurrency the more money is made." Mursch said a campaign from September that used the Showtime website to deliver cryptocurrency-mining ads is another example of attackers targeting a video site.
To add insult to injury, the malicious JavaScript in at least some cases was accompanied by graphics that displayed ads for fake AV programs, which scam people out of money and often install malware when they are run.
The above ad was posted on Tuesday. Like the ads analyzed by Trend Micro and posted on social media, it mined Monero coins on behalf of someone with the Coinhive site key of "h7axC8ytzLJhIxxvIHMeC0Iw0SPoDwCK." It's not possible to know how many coins the user has generated so far. Trend Micro said the campaign started January 18. In an e-mail sent as this post was going live, a Google representative wrote:
Mining cryptocurrency through ads is a relatively new form of abuse that violates our policies and one that we’ve been monitoring actively. We enforce our policies through a multi-layered detection system across our platforms which we update as new threats emerge. In this case, the ads were blocked in less than two hours and the malicious actors were quickly removed from our platforms.
It wasn't clear what the representative meant when saying the ads were blocked in less than two hours. Evidence supplied by Trend Micro and on social media showed various ads containing substantially the same JavaScript ran for as long as a week. The representative didn't respond to follow-up questions seeking a timeline of when the abusive ads started and ended.
As the problem of Web-based cryptomining has surged to almost epidemic proportions, a variety of AV programs have started warning of cryptocurrency-mining scripts hosted on websites and giving users the option of blocking the activity. While drive-by cryptocurrency mining is an abuse that drains visitors' electricity and computing resources, there's no indication that it installs ransomware or other types of malware, as long as people don't click on malicious downloads.
This post was updated to add comment from Google.
https://arstechnica.com/information...-ads-with-cpu-draining-cryptocurrency-miners/
Cryptojacking craze that drains your CPU now done by 2,500 sites
Android apps with millions of Google Play downloads also crash the party
A researcher has documented almost 2,500 sites that are actively running cryptocurrency mining code in the browsers of unsuspecting visitors, a finding that suggests the unethical and possibly illegal practice has only picked up steam since it came to light a few weeks ago.
Willem de Groot, an independent security researcher who reported the findings Tuesday, told Ars that he believes all of the 2,496 sites he tracked are running out-of-date software with known security vulnerabilities that have been exploited to give attackers control. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. About 80 percent of those sites, he added, also contain other types of malware that can steal visitors' payment card details.
"Apparently, cyberthieves are squeezing every penny out of their confiscated assets," he said.
One of the affected sites is shop.subaru.com.au. When I visited the site on Tuesday, the fan on my MacBook Pro, which I hadn't heard in months, soon started whirring. The activity monitor showed that about 95 percent of the CPU load was being consumed. As soon as I closed the site, the load dropped to about 9 percent. Besides putting a noticeable strain on my computer, the site also draws additional electricity from my office. The arrangement allows the attackers to reap the benefit of my hardware and electricity without providing anything to me in return. A recent report from security firm Trustwave's SpiderLabs estimated that the electricity cost for a single computer could range from about $2.90 to $5 per month, presumably if the cryptomining page was left open and running continuously over that time. The figure doesn't include the wear and tear on hardware as it performs complex mathematical problems required to generate the digital coins.
A surge of sites and apps are exhausting your CPU to mine cryptocurrencyThe site that makes all of this possible is Coinhive.com, which Ars covered last week. It offers an easy-to-use programming interface that any website can use to turn visitors' computers into vehicles for generating—or in the parlance of cryptocurrency people, mining—Monero. Coinhive gives participating sites a tiny cut of the proceeds and pockets the rest. Coinhive doesn't require that sites provide any notice to users.
de Groot said that about 85 percent of the 2,496 sites he tracked are generating currency on behalf of just two Coinhive accounts. Depending on the total number of visitors, the amount of time they stay on an affected site, and the power of their computers, the revenue collected by those accounts could be considerable, as would be the total amount of additional charges those accounts made to visitors' electric bills. The remaining 15 percent were spread over additional Coinhive accounts, but de Groot has evidence suggesting those accounts are controlled by a single individual or group. Most of the affected sites concealed the connection to Coinhive by adding a link to the domain siteverification.online or one masquerading as a Sucuri firewall. Those disguised sites, in turn, hosted the crypto-mining JavaScript that interacted with Coinhive.
de Groot's findings suggest that drive-by cryptomining has grown more widespread in the week since Ars first covered it or at least that the phenomenon shows no signs of abating. The earlier Ars article cited research from security firm Sucuri that found 500 sites running hacked versions of the WordPress content management system that were participating in the Coinhive mining. Ars also reported that two Android apps with as many as 50,000 downloads from Google Play had recently been caught putting cryptominers inside hidden browser windows. On Wednesday, researchers from Ixia reported finding two additional such apps with as many as 15 million downloads combined. (In fairness, one of the apps informed users it would use their phone's idle time to generate coins and provided a way for that default setting to be turned off. The apps have since been modified to curtail the practice.)
There are other indications that the in-browser cryptomining racket is getting worse. In a report published Tuesday, endpoint security provider Malwarebytes said that on average it performs about 8 million blocks per day to unauthorized mining pages.
People who want to avoid these cryptojacking scams can use Malwarebytes or another antivirus program that blocks abusive pages, install this Chrome extension, or update their computer host file to block coinhive.com and other sites known to facilitate unauthorized mining. As the phenomenon continues to grow and attract copycat services, blocklists will likely have to be updated, requiring regular updates to blocklists as well
https://arstechnica.com/information...s-cpus-picks-up-steam-with-aid-of-2500-sites/